Table of contents
- What Are Response Plans ?
- ES Doesn’t Come Empty-Handed
- Response Plan Creation/Edition
- Investigation Types
- Investigation Integration
- Conclusion
Here is a second post about Splunk Enterprise Security 8.0.2, released on January 22nd. This time, I will give you an overview of the Response Plans feature.
You can access to Responses Plans by going to Splunk Enterprise Security > Security Content > Response Plans.
What Are Response Plans ?
The Splunk documentation says :
“Create response plans to help document your security operating procedures and standardize the tasks and phases that analysts complete while they respond to investigations in Splunk Enterprise Security. A response plan is a template of guidelines for analysts to follow so that they can provide a standardized response for investigations of the same type.”
Response plans describe the procedures usable by analysts when they investigate detections and alerts. Response plans can be created by users to match SOC needs.
ES Doesn’t Come Empty-Handed
Splunk provides you with eight builtin plans:
- Data Breach
- NIST 800-61
- Suspicious Email
- Generic Incident Response
- Network Indicator Enrichment
- Self-Replicating Malware
- Vulnerability Disclosure
- Account Compromise
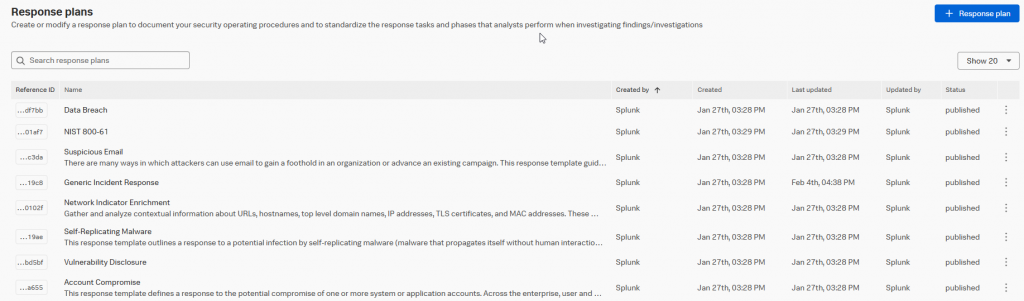
Built-in Response Plans cannot be edited, but they can be copied. If you do so, you can add, edit, or delete parts of the Response Plan to adapt it to your needs.
Response Plan Creation/Edition
A response plan is divided into phases, with primary tasks within.
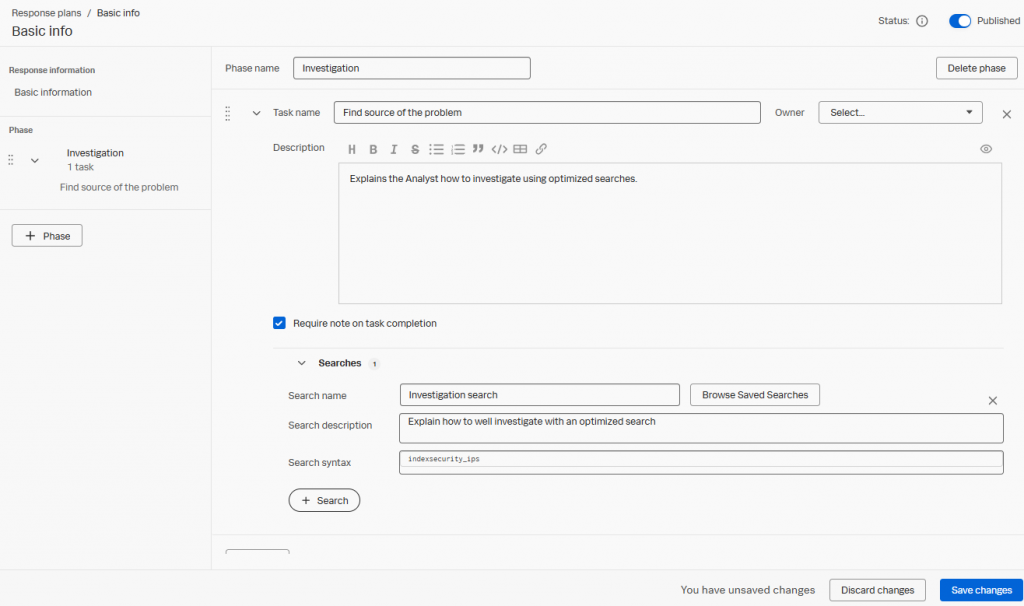
You can even define searches to help analysts when defining your response plan. You can add multiple Searches, Tasks, and Phases to build a complete procedure. Phases, Tasks, and Searches can be reorganized.
Once you have defined your response plan and published it, you can associate an investigation type with it.
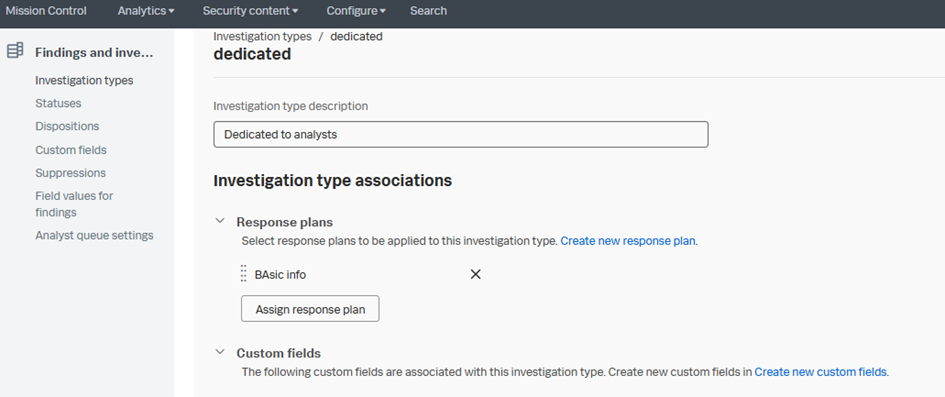
Investigation Types
You can define different investigation types. The response plans can then be assigned to investigation types. To setup investigation types, go to Splunk Enterprise Security > Configure > Findings and investigations.
Investigation Integration
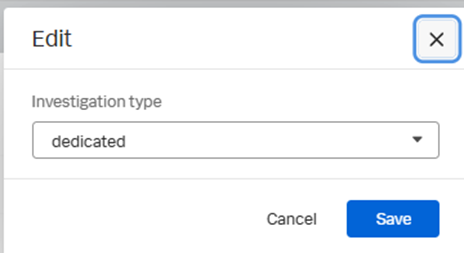
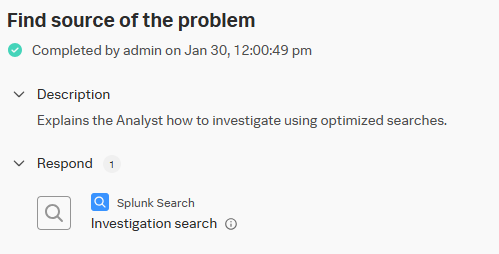
When you open a new investigation on a new event, you can retrieve the investigation type. It’s “default” by default, but when you change it to another investigation type, you find the phases and tasks entered previously:
Once done, when you assign an Investigation Type to a finding, you will get the associated Response Plan and will see the Phases/Tasks/Searches directly in your investigation. You can use the magnifying glass button to launch every search you prepared in the Response Plan. Results will be displayed within the Search tab of the Investigation:
Investigation type can be changed on the Info panel on the right of your investigation.
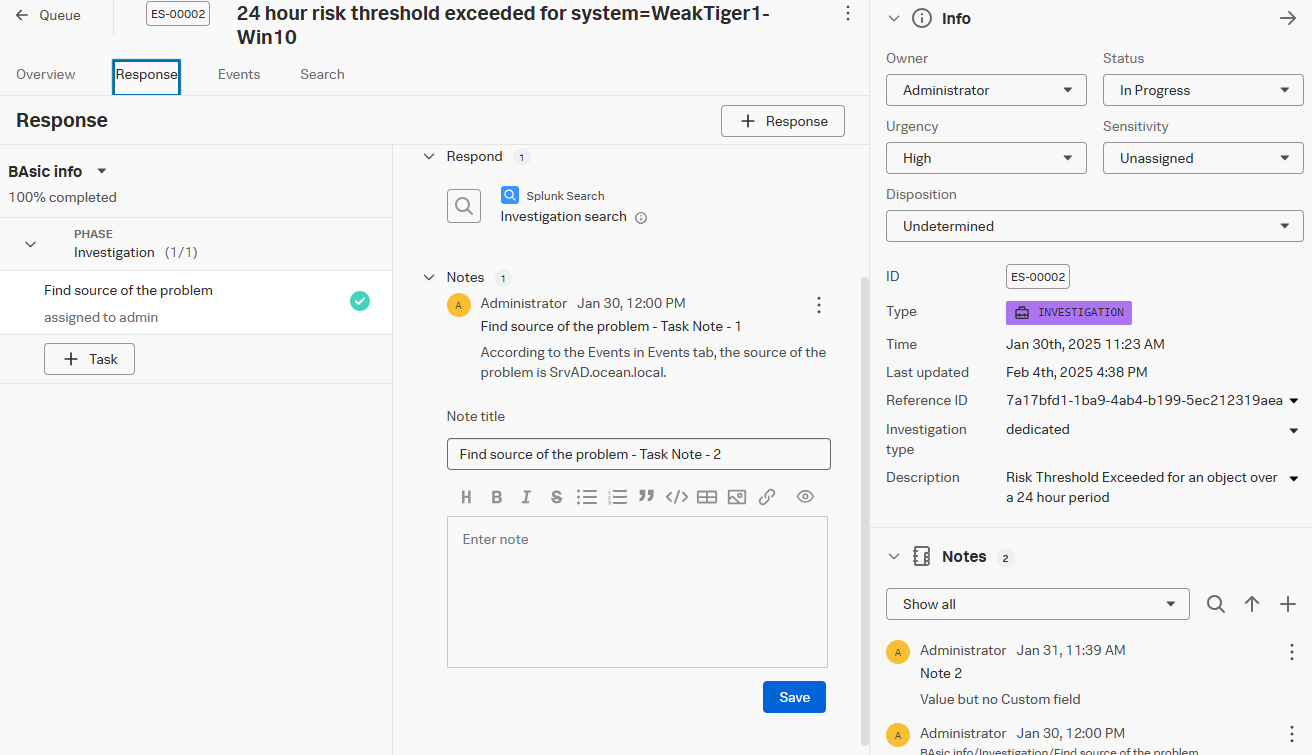
You can stick to the strict Response Plan defined for that investigation type, but you can also add tasks within your investigation. Additionally, you can indicate when a task starts or ends. When you start one, it is automatically assign to you.
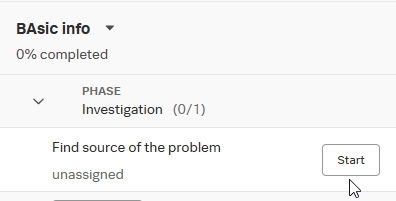
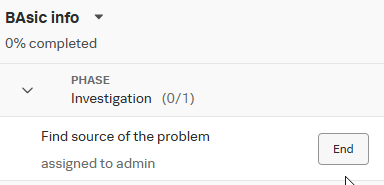
This makes it easier to collaborate with colleagues on an investigation, as you can track the progress and see who completed each step.
Conclusion
The Response Plans feature is a good and refreshing feature included with Splunk Enterprise Security. It clearly doesn’t replace a SOAR or a SIRP, but it gives the opportunity to centralize documentation, procedures, and searches to help analysts in threat detection and analysis, without the need for an external tool or database. The drawbacks are that this is closely linked to built-in Splunk ES Investigations, and that there are no export/import functions.
Additional info :
https://www.splunk.com/en_us/resources/videos/splunk-enterprise-security-8-response-plans.html
https://docs.splunk.com/Documentation/ES/8.0.2/Admin/CreateResponsePlans
